Elastx Identity
The purpose of Elastx Identity is to provide a Single Sign-on experience for access to the different Elastx service offerings. Available as a tech preview, the service provides integration with OpenStack IaaS to enable usage/enforcement of multi-factor authentication.
Join tech preview
If your organization is interested in taking part of the tech preview, submit a request through the Elastx Support page.
Once enrolled, all or selected users will receive an email to verify their account and setup multi-factor authentication.
Before joining the tech preview, please review known issues and limitations.
Update account settings
Users in organizations which have enrolled for tech preview can use the “My Account” web page to change their password, configure multi-factor authentication and similar account related settings.
Supported MFA methods
In addition to username and password for authentication, the tech preview provides the ability to configure multi-factor authentication using either TOTP, supported by mobile applications such as “Google Authenticator” and “FreeOTP”), or the Webauthn standard which enables usage of hardware tokens such as the Yubikey.
TOTP is default method for all accounts (except if explicitly defined otherwise for the organization), but can be changed by the user after initial setup.
OpenStack authentication flow
Once enrolled in the tech preview, users can login to the OpenStack web dashboard (Horizon) by selecting “elastx-id” in the “Authenticate using” drop-down menu and pressing “Connect”:
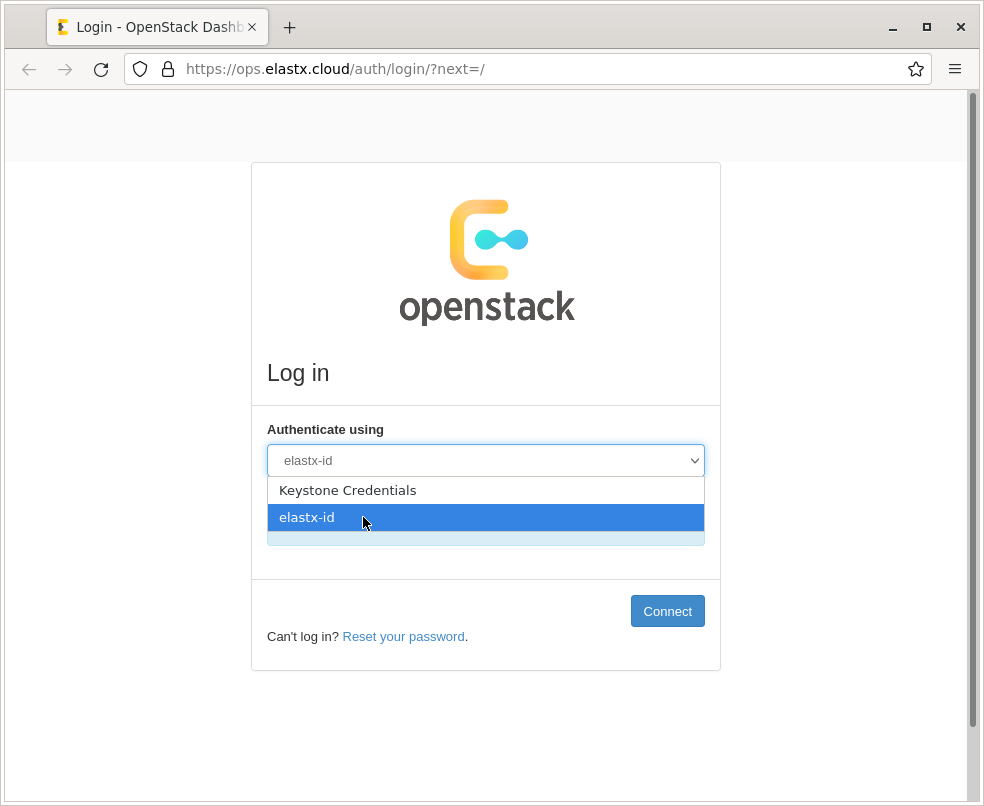
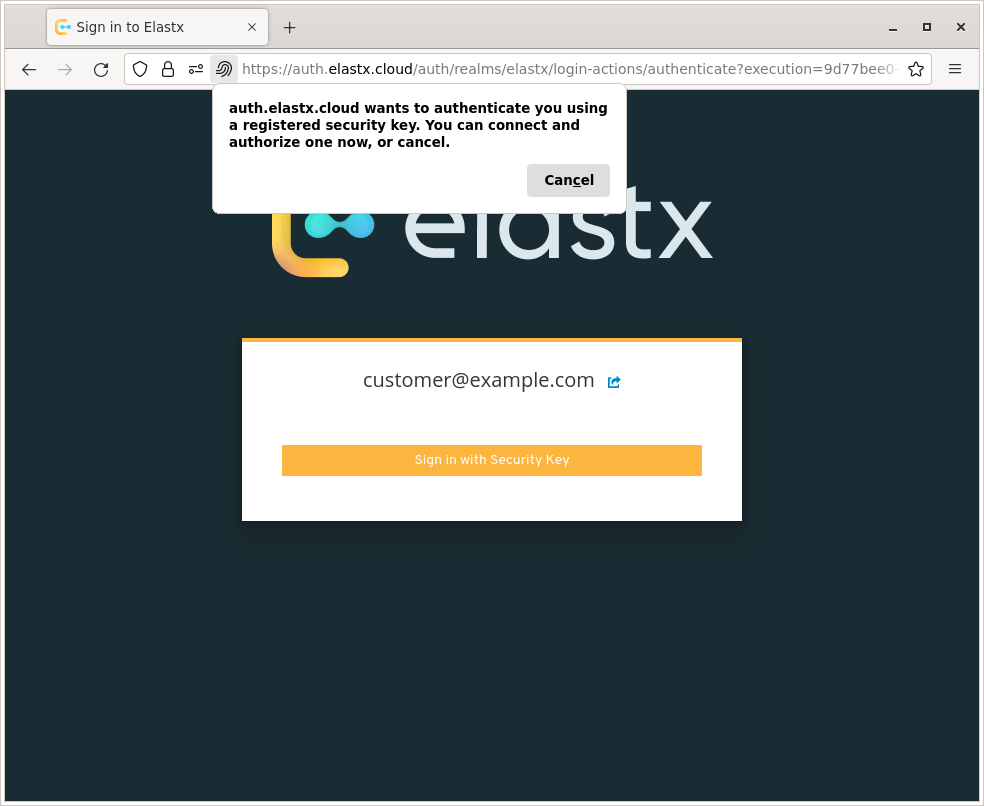
The users are redirected redirected to the login portal, which validates their password/second-factor and redirects them back to the OpenStack dashboard.

Known issues/limitations
During the tech preview phase, the OpenStack platform is configured to support authentication and account management using both platform-specific features (Keystone/Adjutant) and those provided by the Elastx identity service.
This configuration enables users to join/leave the tech preview and still interoperate with each other. As a consequence, it does however affect some functionality that may not work as expected for users in the tech preview.
The following sections describe known issues, limitations and relevant workarounds.
Mandatory usage of MFA
All users enrolled in the tech preview are required to configure both a password and a second factor for authentication. Enforcement of MFA for all non-services users is planned once the service becomes generally available.
CLI and Terraform usage
Applications that use the OpenStack APIs directly, such as the official CLI utilities, Terraform and similar automation tools, do not support authentication using the identity provider. For these use-cases, a dedicated service account or usage of application credentials is highly recommended.
Logout functionality in Horizon
Once a user who has authenticated through the Elastx Identity service logs out of the OpenStack web dashboard (Horizon), their browser session token remains valid for a short period of time. This issue has been mitigated in later versions of OpenStack and the only currently available work-around is to manually clear all browser cookies for the “ops.elastx.cloud” origin.
User settings and project management
Users enrolled for the tech preview can not utilize functionality exposed through the OpenStack web dashboard for account management, such as change/reset password features. These actions may instead be performed through the “My Account” web page.
While the ability for project moderators to invite other users to their projects still exist, it should be noted that new users won’t be automatically enrolled in the tech preview.
Full credential reset
Users in the tech preview can initiate a password reset by clicking on the “Forgot Password?” link below the login form. The password reset flow requires that user authenticate using their second-factor before proceeding.
If the user has lost access to their second-factor (multiple can be configured as a backup), Elastx Support must be contacted for additional identity validation before both credentials are reset. This process is by design for security reasons, but may be reconsidered before the service is generally available.